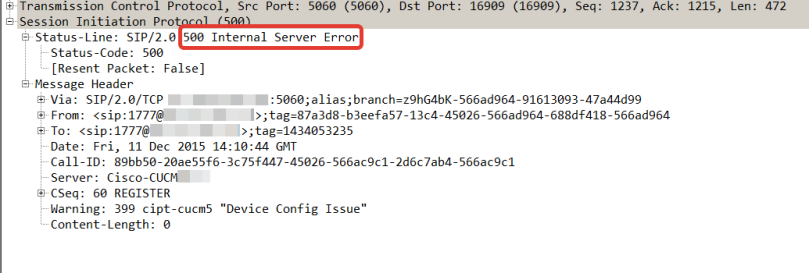
In RTMT there is a separate menu named “Alert Central”, where all active and history alarms of CUCM and IM&P nodes are listed. RTMT communicates with Cisco AMC service to get this info anomg other real-time data.
Service parameters for Cisco AMC looks like that:
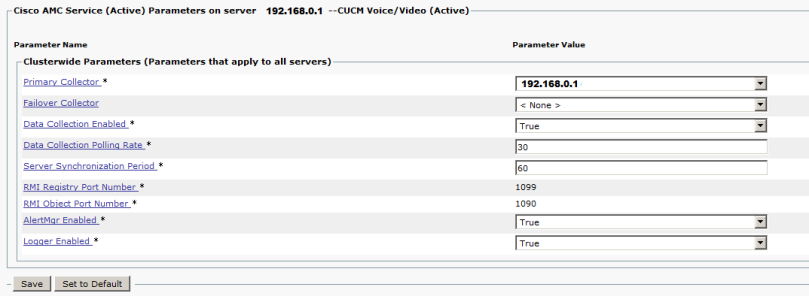
Primary collector is a node (CUCM or IM&P) which would collect logs from other nodes. Cisco suggest to choose least busy node for it. After changing Primary collector AMC service should be restarted on every node.
Logger enabled switch allows AMC logs to be saved as csv files that can be queried later.
Alert files can be found on Primary collector by issuing CLI command
file list activelog cm/log/amc/AlertLog
Files in this directory are generated at midnight every day or when AMC is restarted and file format is AlertLog_MM_DD_YYYY_HH_MM.csv (last part of HH_MM is usually 00_00 or 00_01).
In order to obtain these files programatically there is a special API for that. Here is a simple python script to get the file with alarms:
import requests
def getOneFile(node,user,passw,filename):
header={'SOAPAction':'http://schemas.cisco.com/ast/soap/action/#LogCollectionPort#GetOneFile'}
raw_xml = """<soapenv:Envelope xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/" xmlns:soap="http://schemas.cisco.com/ast/soap/">
<soapenv:Header/>
<soapenv:Body>
<soap:GetOneFile soapenv:encodingStyle="http://schemas.xmlsoap.org/soap/encoding/">
<FileName xsi:type="get:FileName" xmlns:get="http://cisco.com/ccm/serviceability/soap/LogCollection/GetFile/">/var/log/active/tomcat/logs/manager.2016-02-11.log</FileName>
</soap:GetOneFile>
</soapenv:Body>
</soapenv:Envelope>""".format(filename)
try:
response=requests.post('https://'+node+':8443/logcollectionservice/services/DimeGetFileService',data=raw_xml,auth=requests.auth.HTTPBasicAuth(user,passw),verify=False,headers = header)
return response.text
except:
return -1
if __name__ == '__main__':
print getOneFile('192.168.0.1','admin','admin','/var/log/active/cm/log/amc/AlertLog/AlertLog_02_08_2016_00_00.csv')
The user, which queries the file might be your administrator Application user with access to AXL applications.
The output should look like this:
Content-Type: text/xml; charset=UTF-8 Content-Transfer-Encoding: binary Content-Id: <80DB2208357F8BD76EE58C1967C79E0D> <soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/" xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"> <soapenv:Body> <ns1:GetOneFileResponse soapenv:encodingStyle="http://schemas.xmlsoap.org/soap/encoding/" xmlns:ns1="http://schemas.cisco.com/ast/soap/"> <DataHandler href="cid:BC0EDD33C6D0C7A1F6286E3691F95332" xsi:type="ns2:DataHandler" xmlns:ns2="DimeGetFileService"/> </ns1:GetOneFileResponse> </soapenv:Body> </soapenv:Envelope> Content-Type: application/octet-stream Content-Transfer-Encoding: binary Content-Id: <BC0EDD33C6D0C7A1F6286E3691F95332> Time Stamp,Alert Type,Alert Name,Alert Message,Monitored Object Name,Severity,PollValue,Action,Node ID,Group ID 1454882401636,0,CriticalServiceDown, Service operational status is DOWN. Cisco Presence Engine. The alert is generated on Mon Feb 08 00:00:01 EET 2016 on node 192.168.0.34., ,2,0,admin@exmaple.com;,192.168.0.34,System 1454882431615,0,CriticalServiceDown, Service operational status is DOWN. Cisco Presence Engine. The alert is generated on Mon Feb 08 00:00:31 EET 2016 on node 192.168.0.34., ,2,0,admin@exmaple.com;,192.168.0.34,System
As you can see the last part of the output is the content of the file with alarms thrown by CUCM and IM&P, where every line start with a timestamp (with milliseconds). So parsing this output is rather simple.
With this in mind you can create a zabbix server check and monitor UC alarm with common software and stop relying to emails and RTMT.