Let’s assu me have a network of 192.168.0.0/24 and we want it to span to another location separated by public internet.
The scheme would look like this:
192.168.0.0/24 - <eth1 ubuntu1 eth0> -public internet- <eth0 ubuntu1 eth1> - 192.168.0.0/24
and we want hosts in left part of this disconiguous network are able to communicate with hosts in right part.
1) Fot it to work we need both eth0 interface on ubuntu1 and ubuntu2 to have routable IP addresses. Let’s assume eth0 on ubuntu1 has 1.1.1.1 and eth0 on ubuntu2 has 2.2.2.2.
2) Load l2tp_eth module
modprobe l2tp_eth
For this module to be loaded at start, edit /etc/modules and add l2tp_eth at the end of the file.
3) Set up a l2tp tunnel and session on both machines:
root@ubuntu1:~# ip l2tp add tunnel tunnel_id 1000 peer_tunnel_id 2000 encap udp local 1.1.1.1 remote 2.2.2.2 udp_sport 6000 udp_dport 5000 root@ubuntu1:~# ip l2tp add session tunnel_id 1000 session_id 3000 peer_session_id 4000 root@ubuntu2:~# ip l2tp add tunnel tunnel_id 2000 peer_tunnel_id 1000 encap udp local 2.2.2.2 remote 1.1.1.1 udp_sport 5000 udp_dport 6000 root@ubuntu2:~# ip l2tp add session tunnel_id 2000 session_id 4000 peer_session_id 3000
To make this setting persistent create a script named l2tp_eth.sh for example, that would contain the configuration above (specific to each host)
and in /etc/network/interface create a post-up job for eth0
auto eth0 iface eth0 inet static address 1.1.1.1 netmask 255.255.255.0 network 1.1.1.0 broadcast 1.1.1.255 gateway 1.1.1.2 dns-nameservers 1.1.1.2 8.8.8.8 post-up /path/to/scipt/l2tp_eth.sh
Don’t forget to make the script executable with
chmod +x /path/to/scipt/l2tp_eth.sh
4) Now you have a l2tpeth0 interface (type ip address show to be sure). It’s time to set up a bridge between internal eth1 and l2tpeth0.
This is how it should look like in /etc/network/interface
auto l2tp_br iface l2tp_br inet static address 192.168.0.11 netmask 255.255.255.0 network 192.168.0.0 broadcast192.168.0.255 bridge_ports l2tpeth0 eth1 bridge_stp off bridge_fd 0 bridge_maxwait 0
I picked 192.168.0.11 as this bridge interface for ubuntu1 and 192.168.0.22 for ubuntu2. If this addess doesn’t shows up after reboot, probably you are missing bridge-utils, that can be installed with apt-getinstall bridge-utilsThese addresses can be used as a GWs for some servers in networks left part to access internet hosts provided NAT is set up with
iptables -t nat -A POSTROUTING -o eth0 -s 192.168.0.0/24 -j MASQUERADE
If you are using virtualized servers with VMware vsphere is’t necessary to allow Promiscuous Mode on vswitch or port group so that eth1 would accept frames destined to other hosts.
5) As L2TP is encapsulated into IP and it itself encapsulates ethernet frames we should tune MTU for packets inside the network.
root@ubuntu1:~# ip link set eth1 mtu 1446
root@ubuntu2:~# ip link set eth1 mtu 1446
That’s it. You can place a server in either part of 192.168.0.0/24 network and they will be able to communicate with each other. I suppose these scheme can be used to turn CWMS HA installation into MDC without buying a license.
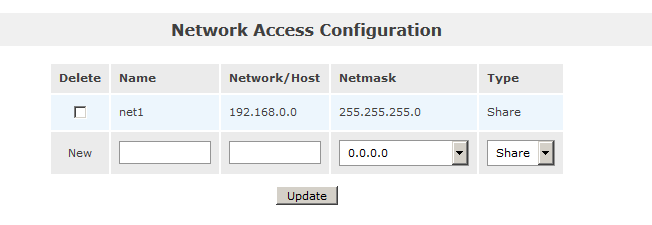
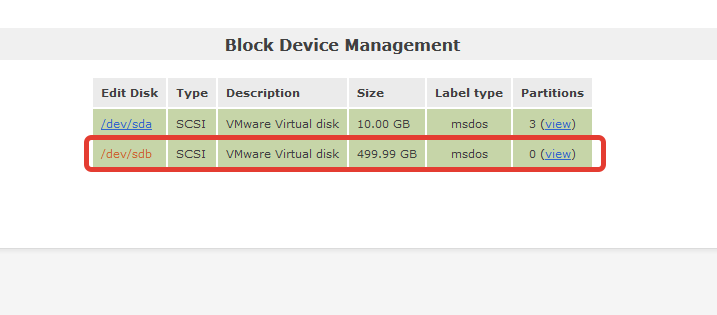
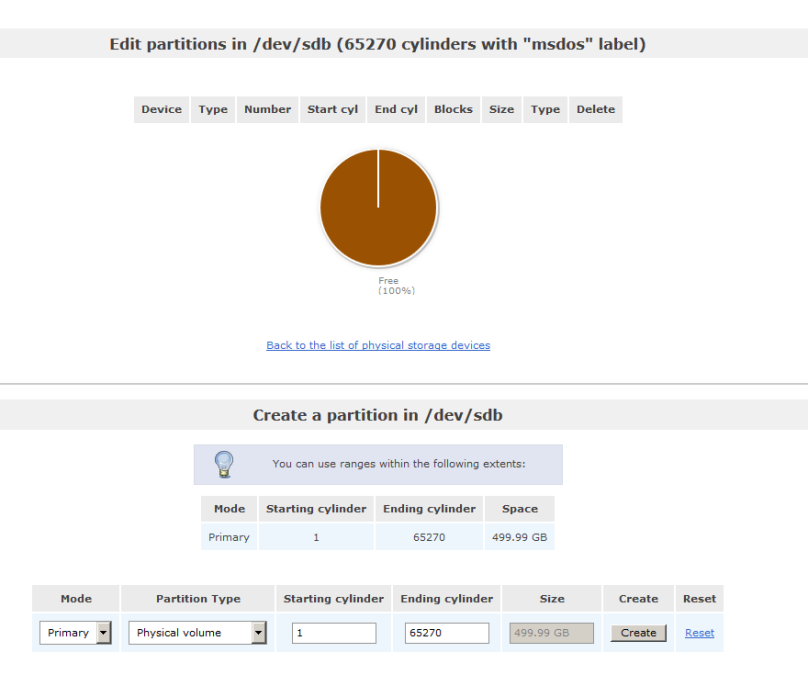
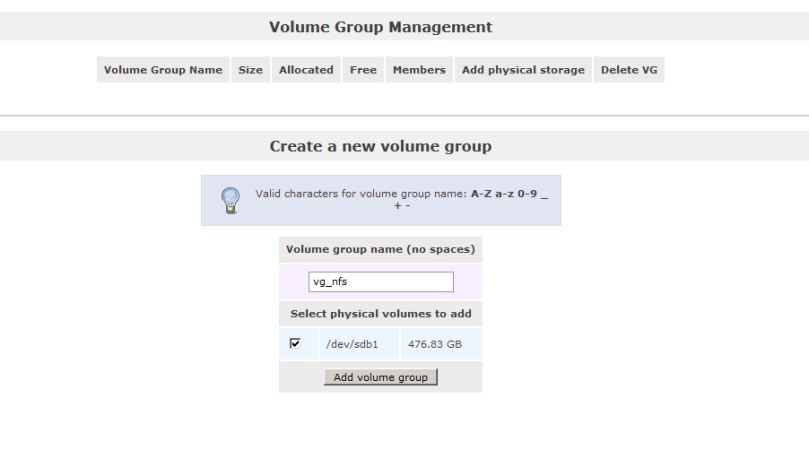
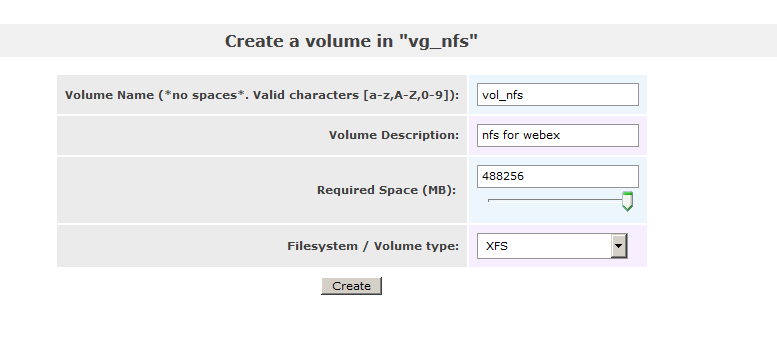
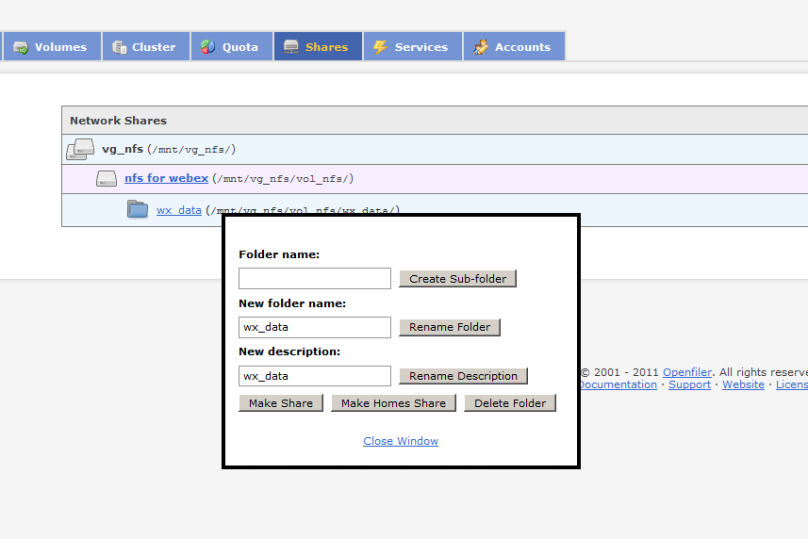
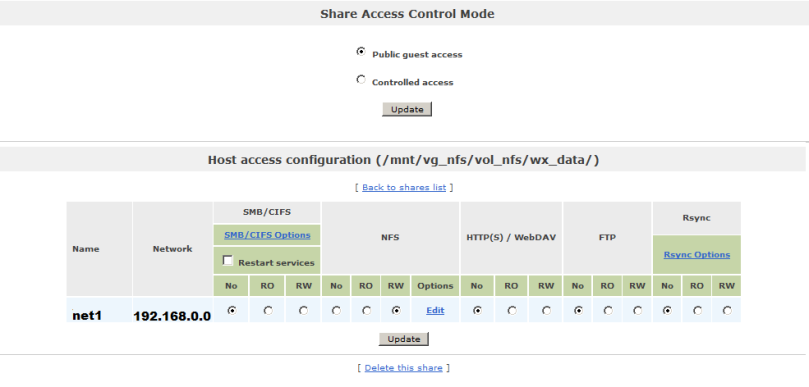
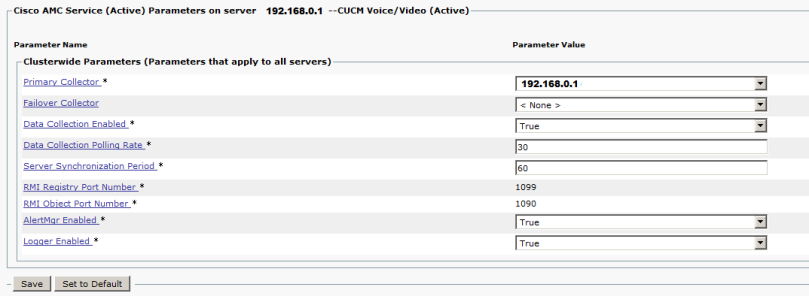
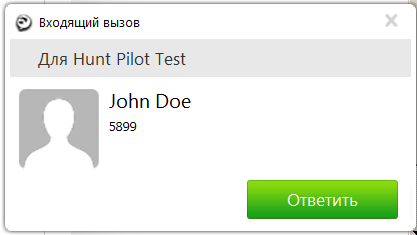
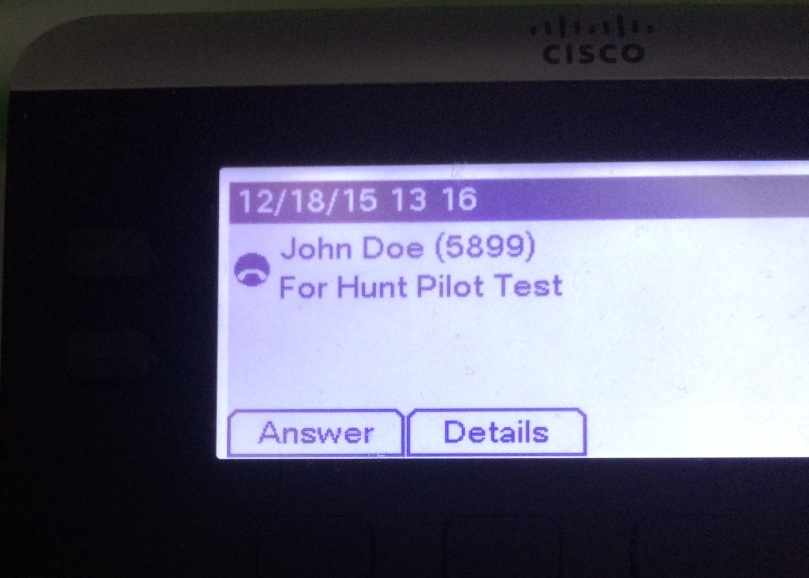
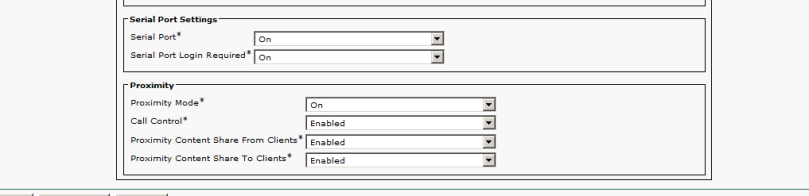 So now we can use BAT to enable Proximity on all devices.
So now we can use BAT to enable Proximity on all devices.